NIST Incident Response Recommendations and Considerations for Cybersecurity Risk Management (NIST SP 800-61r3) has been released. This document puts forward new strategies for addressing cybersecurity incidents with systematic responses that minimize loss of data and service. It provides an incident response life cycle model that is more fitting to the present risk environment.
Incident Response Life Cycle
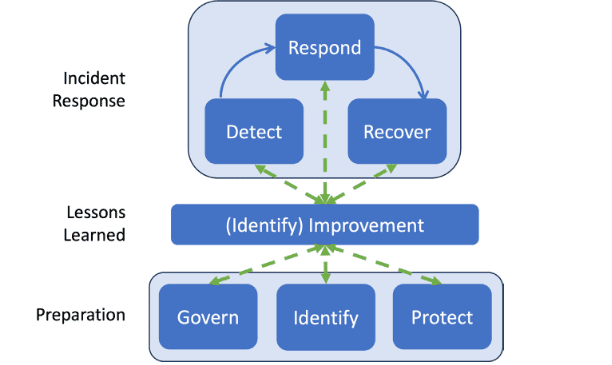
In this revision NIST stresses the need for continuous improvement of cybersecurity risk management processes to counter an ever changing threat environment. It calls for using three functions (Govern, Identify, and Protect) to prevent and prepare for handling incidents that occur. These functions preform broad risk management activities to support incident response.
Govern (GV) establishes, communicates, and monitors the organization’s risk management strategy. Identify (ID) ensures that that current risks are understood so through asset management, risk assessments, and improvements for response processes. Protect (PT) implements safeguards to manage risks.
Three other functions, Detect Respond, and Recover, are then used to discover, contain, eradicate, and recover from incidents. These specific functions detail the monitoring, reporting, prioritization, analysis, and restoration of data and data systems.
As shown in the figure below, continual improvement is gained by lessons learned. These lessons can then inform risk management functions as to how best to change detect, response, and recovery procedures to adapt to the current threat environment.
Incident Response Roles and Responsibilities
More emphasis has been placed in this revision to roles and responsibilities beyond those of incident handlers. Current roles identified include leadership, technology professionals, legal experts, public affairs officials, human resources, facility security and management staff, and asset owners.
Responsibilities for these roles should be documented in statements of management commitment, policies, determination of scope, guidelines, and performance measures. Procedures should be explain how all roles are to work together in response to common threats and incidents.
Conclusions
The NIST incident response recommendations put forth in NIST SP 800-61r3 illustrate the importance of involvement of upper management in cybersecurity practices. Continuous improvement that is adaptive to changing risk scenarios can take place when findings are reviewed in a management perspective.
CVG Strategy Access Control Signs, Badges, and Visitor Logs
CVG Strategy’s Signs & Badges Store has a variety of signs, badges, and visitor logs to help your organization meet its physical and environmental security requirements. These offerings provide solutions for both export compliance and cybersecurity.



